IT Security Tools
File Backups
Backups are useful primarily for two purposes. The first is to restore a state following a disaster (called disaster recovery). The second is to restore small numbers of files after they have been accidentally deleted or corrupted.
File Backups for Students
Students can access campus computers using their network ID. Once students log off all the work saved on the computer is lost. Students enrolled at SUSLA are licensed to use Microsoft OneDrive (part of the Microsoft Office 365 suite). The size of shared drive is limited to 1 TB (terabyte) of space. This storage is accessible from any computer connected to the internet.
File Backups for Faculty/Staff
On your work computer, you need not worry about having to reinstall your operating system or any other supported products. Information Technology Center will do that for you. However, you may need to keep copies of any special products you purchase. Like students, faculty/staff can regularly back-up any personally created files to their Microsoft OneDrive cloud storage. In addition, network file sharing is offered for faculty/staff as well. A job request would have to be submitted to the Information Technology Center before a shared network drive is made available for use.
Back-up Options
USB Flash Drives - USB flash drives are easily removable and most weigh less than 1 ounce, but usually offer less storage space than USB external drives.
USB External Drive - USB external drives are easily removable and offer higher storage options than a USB flash drive, however they can be cumbersome at times.
Log Out or Lock Your Computer
Forgetting to log out poses a security risk with any computer that is accessible to other people (including computers in public facilities, offices, and shared housing) because it leaves your account open to abuse. Someone could sit down at that computer and continue working from your account, doing damage to your files, retrieving personal information, or using your account to perform malicious actions. To avoid misuse by others, remember to log out of or lock your computer whenever you leave it.
Before you step away from your computer for more than a minute, here are some quick ways to lock your computer:
On a Windows Computer
Press Ctrl+Alt+Del keys together. Click Lock Computer.
Or
Press Windows+L key together.
Passwords
Best Practices for Password Protection
- Always use strong passwords. For more information, see Strong passwords.
- If passwords must be written down on a piece of paper, store the paper in a secure place and destroy it when it is no longer needed.
- Never share passwords with anyone.
- Use different passwords for all user accounts.
- Change passwords immediately if they may have been compromised.
- Be careful about where passwords are saved on computers. Some dialog boxes, such as those for remote access and other telephone connections, present an option to save or remember a password. Selecting this option poses a potential security threat.
A weak password:
- Is no password at all.
- Contains your user name, real name, or company name.
- Contains a complete dictionary word. For example, Password is a weak password.
A strong password:
- Is at least seven characters long.
- Does not contain your user name, real name, or company name.
- Does not contain a complete dictionary word.
- Is significantly different from previous passwords. Passwords that increment (Password1, Password2, Password3 ...) are not strong.
- Contains characters from each of the following four groups:
| Group | Example |
|---|---|
| Uppercase letters | A, B, C … |
| Lowercase letters | a, b, c … |
| Numerals | 0, 1,2, 3, 4, 5, 6, 7, 8, 9 |
|
Symbols found on the keyboard (all keyboard characters not defined as letters or numerals) |
` ~ ! @ # $ % ^ & * ( ) _ + - = { } | \ : " ; ' < > ? , . / |
Virus Protection
You can protect your computer from virus attack by following some simple rules.
Top ways to prevent a virus from infecting your computer:
- Have at least one anti-virus program installed.
- Maintain up-to-date virus protection software on your computer.
- Don't install applications from sites you don't trust 100%!
- Be careful opening e-mail attachments. Do not open an e-mail attachment unless you are expecting it or have checked with the sender.
- Remove all open shares from your computer system.
- Visit only legitimate business Web sites. And do not click on links in unsolicited e-mail messages.
- Use strong passwords wherever possible.
- Run Virus scans at least weekly and if heavy Internet user than twice a week.
- Common Sense is always the best weapon...
Pop-Up Blockers
Many legitimate advertisers on the Internet use windows that pop up in the middle of your screen to display a message. They might also open when you click a link or button on a Web site, and they might open either over or under the window you wish to view. Some pop-ups are helpful. For example, if you click an image to see a larger version, it might open in a pop-up window. Unfortunately, some pop-up windows can contain inappropriate content or can be a way for you to accidentally download dangerous software (called spyware or adware) onto your computer.
Microsoft has included a pop-up blocker in its latest versions of Internet Explorer, set to a medium blocking level, which means it will block most ads.
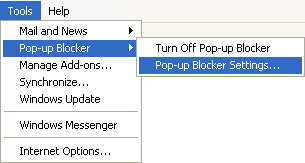
To change Pop-up Blocker settings:
- Open Internet Explorer.
- On the Tools menu, point to Pop-up Blocker, and then click Pop-up Blocker Settings.
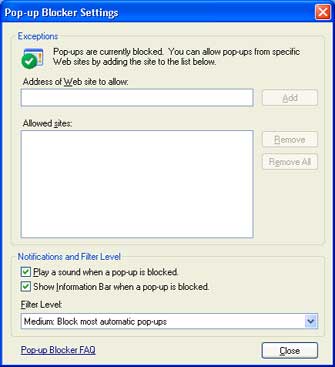
If you want to see pop-up windows from a specific Web site, type the address (or URL) of the site in the Address of Web site to allow box, and then click Add.
Tip To temporarily allow a site to display pop-ups, click the Information Bar when it notifies you that a pop-up has been blocked. Then click Temporarily Allow Pop-ups.
Phishing and Pharming
Both pharming and phishing are methods used to steal personal information from unsuspecting people over the Internet.
Phishing typically involves fraudulent bulk e-mail messages that guide recipients to legitimate-looking but fake Web sites and try to get them to supply personal information like account passwords.
Pharming tampers with the domain-name server system so that traffic to a Web site is secretly redirected to a different site altogether, even though the browser seems to be displaying the Web address you wanted to visit.
To help avoid pharming, make sure the Web site has a valid certificate of authority, from a service like VeriSign, that matches the site's name before you enter any personal data.
How to protect your network, servers, pcs and mobile devices from phishing and pharming:
- Keep all browser, email, and IM security patches up to date.
- Be skeptical. Do not rely on personal discernment to distinguish between legitimate and unlawful requests for confidential information.
- Never surrender personal or confidential information to an unfamiliar or unknown individual or business.
- Delete any email that requests confidential information.
- If the request appears legitimate, use an established phone number to verify the request.
- Do not disable enterprise antivirus, anti-phishing, firewall, or other security protection.
- Seek IT counsel and support if you experience any communication (via email, phone, fax, or instant message) that requests corporate or personal information.
What may happen if you don't adequately protect your technology assets from phishing and pharming:
- Intellectual property theft—with potentially devastating financial results.
- Compromised (sometimes irrevocably) market position.
- Damaged corporate credit and reputation.
Spam E-Mail Filtering
E-mail spam, also known as junk e-mail, is a subset of spam that involves nearly identical messages sent to numerous recipients by e-mail. The Spam Filter identifies and blocks spam messages that come from the Internet. You can review the list of blocked messages, send blocked messages to your e-mail inbox, and customize the spam filters for your personal e-mail.
